NO_MORE_RANSOM - how to decrypt encrypted files?
At the end of 2016, the world was attacked by a very trivial virus-a Trojan that encrypts user documents and multimedia content, called NO_MORE_RANSOM. How to decrypt files after effects of this threat, and will be considered further. However, it is worth to warn all users subjected to the attack that a single methodology is not. This is connected with one of the most advanced encryption algorithms, and the degree of penetration of the virus into the computer system or even to a local network (though initially on a network effect and it is not designed).
What kind of virus NO_MORE_RANSOM and how does it work?
In General, the virus itself usually attributed to the Trojans class type I Love You, that penetrate into a computer system and encrypts user files (usually multimedia). However, if the progenitor was distinguished only by the encryption, this virus is very much borrowed from the once-notorious threat called DA_VINCI_COD, combining in itself the functions of a blackmailer.

Once infected, most files audio, video, graphics or office documents are assigned a long name with extension NO_MORE_RANSOM containing a complex password.
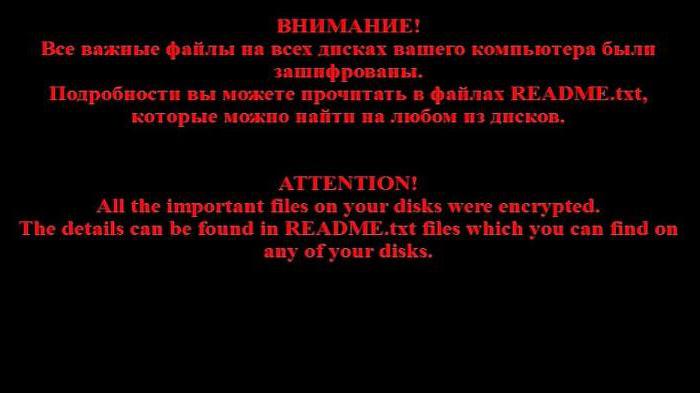
When you try opening them on the screen, a message appears stating that the files have been encrypted and to decrypt you have to pay a certain amount.
How the threat gets into the system?
Let us Leave alone the question on how after effects NO_MORE_RANSOM decrypt files of any of the above types, please refer to the technology penetration of the virus into the computer system. Unfortunately, as corny as it may sound, it uses old-fashioned way: by e-mail, a letter arrives with an attachment, opening which, the user and receives the triggering malicious code.
Recommended
How to get out of "Skype" on the "Android" and not only
How to get out of "Skype" "Android"? This question bothers many users. The thing is that the messenger is not so difficult. But there are features that are only for mobile versions. To log out of Skype in this case more difficult than it seems. But i...
Kingo ROOT: how to use the program to gain administrative rights on Android
The Gadgets on the platform Android regained the lion's share of the market. Developers are continually perfecting the OS, trying to fit the needs of the users, but from year to year admit palpable mistake: forbid the owner to "stuffing" of his gadge...
How to get from Stormwind to Tanaris: practical tips
World of Warcraft is an iconic MMORPG, uniting millions of players around the world. There are many locations and puzzles, secret trails and larger, but rather dangerous paths. Sooner or later, every player chose the side of the Alliance, we have to ...
Originality, as you can see, this method is no different. However, the message may be disguised as a meaningless text. Or, on the contrary, for example, if we are talking about large companies, under changing conditions of a contract. It is clear that the average clerk opens the attachment, and then receives poor results. One of the brightest flares became database encryption popular package 1C. And this is a serious matter.
NO_MORE_RANSOM: how to decipher the documents?
But all the same it is necessary to turn to the main issue. Surely everyone wants to know how to decrypt the files. Virus NO_MORE_RANSOM has its own sequence of actions. If the user attempts to perform a decryption immediately after infection to do this you. If the threat settled in the system firmly, alas, without the help of professionals can not do. But they are often powerless.
If the threat was discovered in a timely manner, only one way – contact the support anti-virus companies (yet not all the documents have been encrypted), send a few not available to open a file and based on the analysis of the originals, stored on removable media, try to restore your documents after saving to the same drive everything else is available to open (although the full assurance that the virus has not penetrated into such documents, either). After that, to be sure, the media must check out at least a virus scanner (who knows what).
The Algorithm
We should also mention the fact that the virus uses for encryption algorithm, RSA-3072, which, in contrast to previously used technology, RSA-2048, is so complex that selection of the right password, even assuming that it will deal with the entire contingent of anti-virus laboratories can take months and years to come. Thus, the question of how to decipher NO_MORE_RANSOM will require quite time-consuming. But what if you restore the information you need immediately? First of all – remove the virus itself.
Can I delete virus and how to do it?
Actually, it is not hard. Judging by the arrogance of the creators of the virus threat to computer system is not masked. On the contrary – she even profitable “auto-delete themselves” after the actions performed.
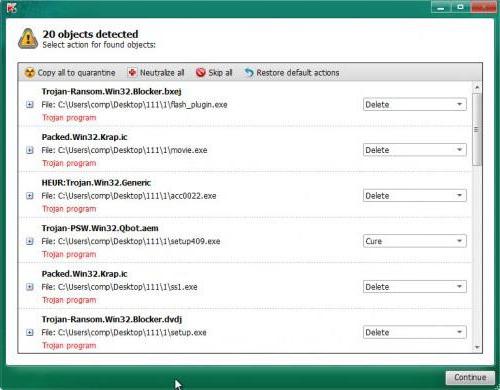
Nevertheless, at first, going on about the virus, it still should be neutralized. The first step is to use a portable protective tools such KVRT, Malwarebytes, Dr. Web CureIt! and the like. Note: used to verify software should be portable type mandatory (no installation on hard drive with the launch of the optimal variant from removable media). If the threat is detected, it must be removed immediately.
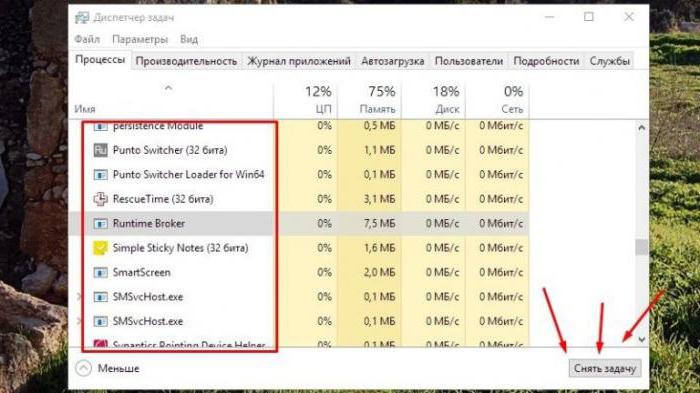
If any of the action, you need to first log in “task” and terminate all the process related to virus, sort the services by name (as a rule, the Runtime Broker process).
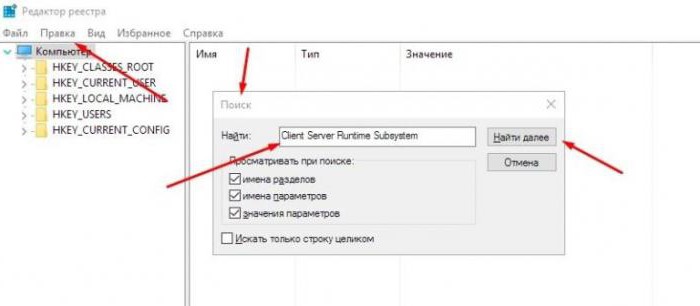
After removing the problem, you need to call the registry editor (regedit in the menu “Run”) and ask search by name “Client Server Runtime System" (without the quotes), and then using the menu move through the results “Find next…" delete all found elements. Next you need to producereboot the computer and believe “task Manager" whether there is the required process.
In principle, the question of how to decrypt the virus NO_MORE_RANSOM on the stage of infection, can be solved with this method. The probability of neutralization, of course, small, but there is a chance.
How to decrypt files encrypted NO_MORE_RANSOM: backups
But there's another method that few people know or even realize. The fact that the operating system itself constantly creates its own shadow backup (e.g. in case of recovery), or the user deliberately creates such images. As practice shows, on such copy, the virus has no effect (in its structure it is simply not available, although deprecated).
Thus, the problem of how to decipher NO_MORE_RANSOM comes down to how to use them. However, to apply the standard tools of the Windows is not recommended (and many users to hidden copies won't have access at all). So apply need utility ShadowExplorer (it is portable).
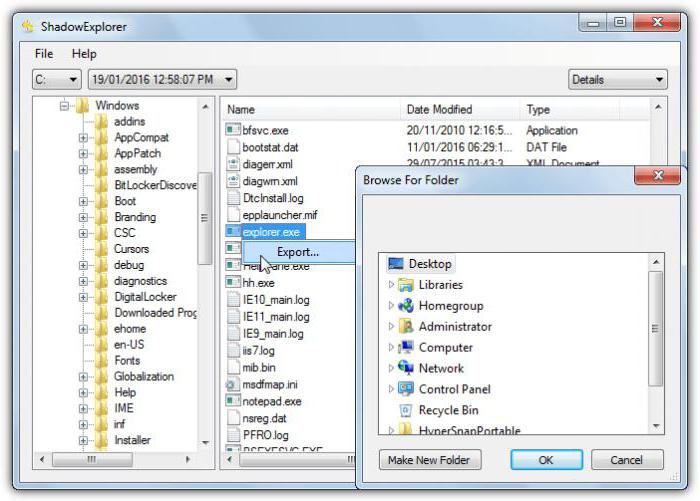
To restore simply run the executable file of the program, sort by date added or sections, select the desired copy (file, folder or entire system) and via the RMB menu, use the string exports. Then simply select the directory in which to store the current copy, and then use the standard restore process.
Third Party tools
Of Course, to the problem of how to decipher NO_MORE_RANSOM, many labs offer their own solutions. For example, «Kaspersky Lab» recommends the use of its own software product Kaspersky Decryptor presented in two versions – Rakhini and Rector.
No less interesting looks and similar design like decoder NO_MORE_RANSOM from Dr. Web. But then you need to consider that the use of such programs is justified only in the case of rapid detection of threats, has not yet been infected all the files. However, if the virus settled in the system steady (when encrypted files are simply impossible to compare the unencrypted originals) and such application may be useless.
Summary
Actually, the conclusion is only one: to fight this virus it is necessary only at the stage of infection, when there is encryption, only the first file. In General, it's best not to open attachments in emails received from dubious sources (it concerns only the clients installed directly on the computer-Outlook, Oulook Express, etc.). In addition, if an employee of the company has at its disposal a list of the addresses of customers and partners, open “left” message becomes completely impractical, since most when applying for a job sign agreements not to disclose trade secrets and cybersecurity.
Article in other languages:
AR: https://www.tostpost.com/ar/computers/1642-no_more_ransom.html
HI: https://www.tostpost.com/hi/computers/1642-no_more_ransom.html
JA: https://www.tostpost.com/ja/computers/1641-no_more_ransom.html
TR: https://www.tostpost.com/tr/bilgisayarlar/2847-no_more_ransom---ifresini-ifrelenmi-dosyalar.html
ZH: https://www.tostpost.com/zh/computers/1776-no_more_ransom.html

Alin Trodden - author of the article, editor
"Hi, I'm Alin Trodden. I write texts, read books, and look for impressions. And I'm not bad at telling you about it. I am always happy to participate in interesting projects."
Related News
How to make a stamp in Photoshop any version
Probably every new user of the software, burrowing deeper and deeper into the wilds of functional programs with delight and astonishment makes more and more open, with gratitude and admiration thinking about the creators of a uniq...
As aprivately door in Minecraft
In single-player mode in "Minecraft," you don't need to worry about what your things are without your supervision, because you need only to close the door, set the fence, and no one monster can't get to you to cause any harm to yo...
Clean your Android from junk and unnecessary files
In the process of operation of any device on the platform “Android” the device's operating system day after day becomes clogged, accumulating a lot of unnecessary information, search history and downloads browser, any ...
A bitwise operation. Programming in C and C++
Bitwise operation is the operation used for performing operations on bit patterns or binary numbers, which include working with individual bits. This is a quick, simple action directly supported by the processor used to manipulate...
iOS 9 for iPhone 4S reviews, description, features, and updates
At the annual WWDC in 2015 were presented for 9 account version of the mobile operating system from Apple. The software was well received and many intrigues, including the support of quite old gadgets, including the iPad 2nd gener...
My family, Windows Phone: customize. Set up My family on Windows Phone
today's mobile phones based on Windows Phone operating system (update every machine depends on its technical characteristics) occupy a considerable segment of the market of mobile phones. I would like to note that they are positio...



















Comments (0)
This article has no comment, be the first!